Are you curious about how Entra ID roles are utilized? Or perhaps you’re wondering if any users or applications have active roles all the time?
Here are some best practices for using privileged roles in Entra ID:
- Apply principle of least privilege
- Use Privileged Identity Management to grant just-in-time access
- Turn on multi-factor authentication for all your administrator accounts
- Configure recurring access reviews to revoke unneeded permissions over time
- Limit the number of Global Administrators to less than 5
- Limit the number of privileged role assignments to less than 10
With that in mind, I’m thrilled to announce that Microsoft has introduced a new feature called “Discovery and Insights” directly inside the Privileged Identity Management pane in Entra ID. This feature is designed to help you identify privileged role assignments across Microsoft Entra and provides recommendations on how to secure them using Microsoft Entra governance features like Privileged Identity Management (PIM).
With this new feature, you can gain a deeper understanding of how Entra ID roles are utilized and whether any users have standing roles all the time. We hope this feature will help you better manage your Entra ID roles and improve your overall security posture.
In the picture below you can see the view of the ‘Discovery & Insights’ page within Entra ID PIM upon accessing it.
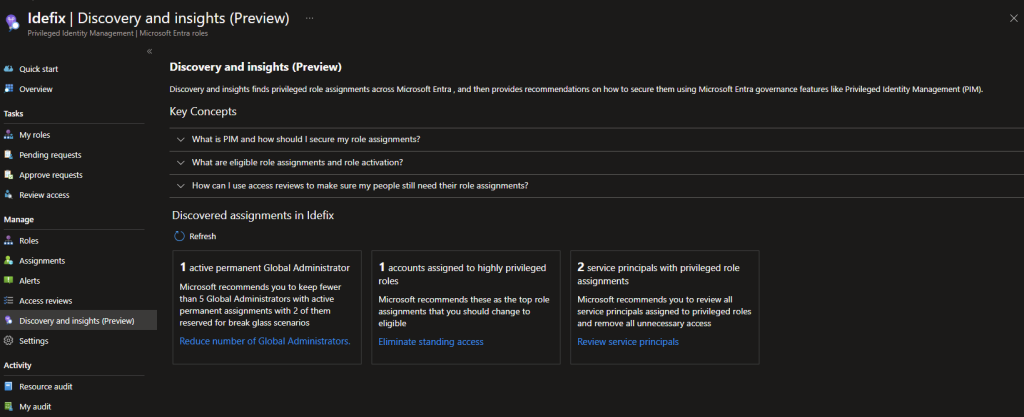
We can immediately view information about active or standing access on Global Administrator roles and other privileged roles
From this page, we can reduce the number of Global Administrators by removing access or changing it to ‘Eligible’ access. At present, my user account is eligible for Global Administrator status, but since I have elevated my account to GA, the insight thinks that I have standing access.
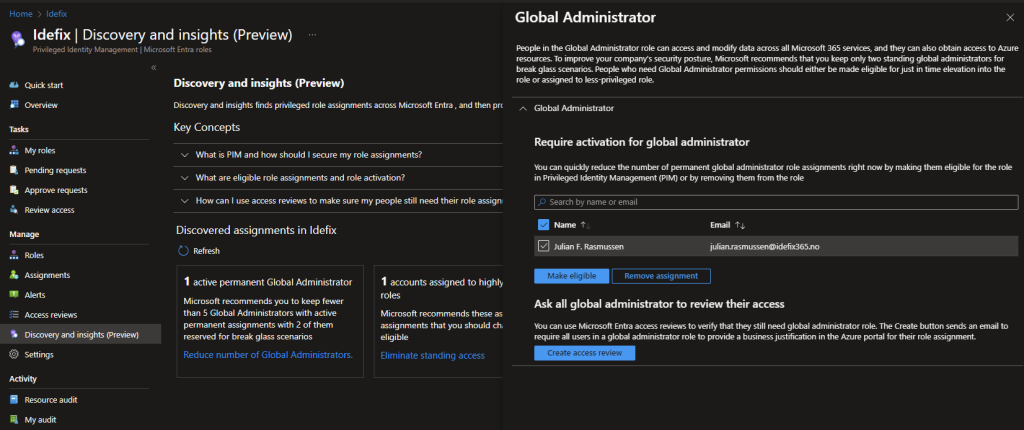
The next page we can look at is the middel one containing accounts that has assigned some highly privileged roles.
A list of privileged role can be found at Microsoft Learn.
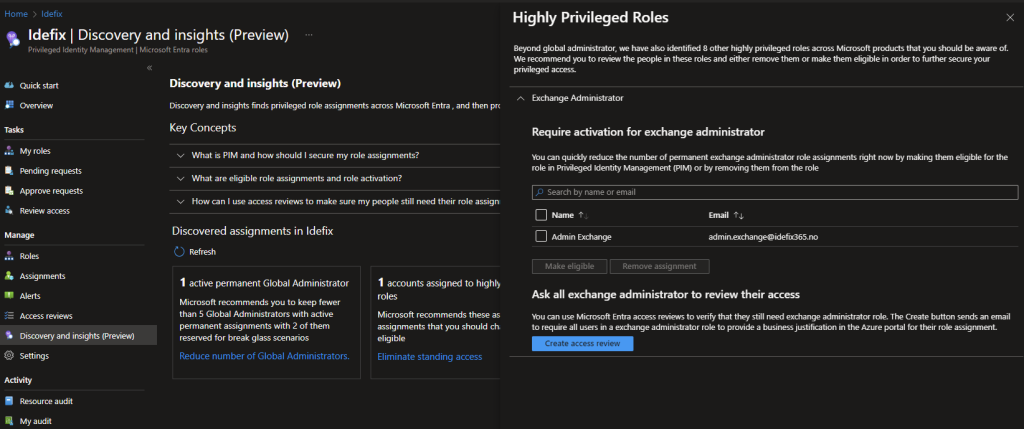
At this view, I only have one account for demonstration purposes. However, we can see that an ‘Exchange Administrator’ role is assigned to an account named ‘admin exchange’. This may be a service account that is required, or we can use this insight to immediately remove access for this account (or make it eligible).
The final page of this report is dedicated to ‘Service Principals with Privileged Role Assignments’. This page is particularly useful as over time, role assignments are often added to Service Principals but are frequently forgotten to be removed when no longer in use.
We can immediately obtain an overview of Service Principals that have privileged roles assigned to them from this page.
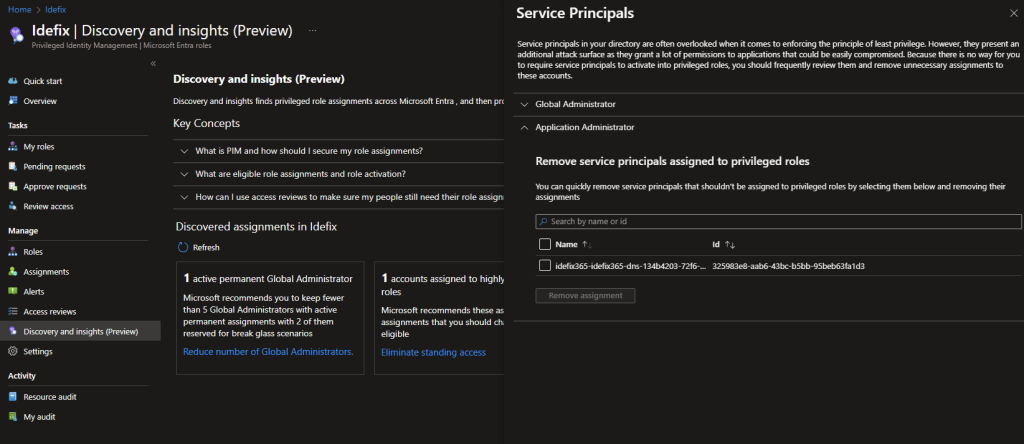
On the last page of this report, we can see that my service principal has been added to two privileged roles: one Global Administrator and one Application Administrator. From this page, we can easily remove access.
So what do you think, is this usefull for you? I think this is super usefull to get an full overview super fast and also the feature that we can remove access or move users over to eligable is super usefull!




