In today’s ever-evolving digital landscape, maintaining security while managing access is paramount. Entra ID Administrative Units (AUs), a pioneering tool to streamline and fortify your organizational security policies. With the latest enhancement—Restricted Management—now in preview, AUs can secure for example conditional access policies to new heights. By securing all excludes from conditional access policies using security groups protected by AUs with restricted management, organizations can ensure that only the right personnel have access to do changes on critical policies. This cutting-edge feature allows for granular control, safeguarding against unauthorized access and potential security breaches. As we delve into the capabilities of Entra ID Administrative Units, you’ll discover how these innovations empower administrators to maintain a robust, secure, and efficient IT environment.
Conditional Access administrators can do changes on the rule and remove or add excludes. But if you are using groups, then in many cases the entire IT Helpdek or even developer teams may do changes on those groups meaning that they can easly exclude users from critical Conditional Access rules.
The first thing we need to have good routines on is who has the ability to elevate to Conditional Access Administrator role. But as I mentioned, if we are using groups in our CA policies we also need to be able to protect who can do changes on those groups so that we ensure that only the right personel can do those changes.
Naming Conventions for Administrative Units
When we think of Administrative units it’s important to remember that we need a good naming convention so that we keep our environment in a good health state.
A naming convention let’s administrators get a overview over the settings that are set without the need for going into the settings.
When adding Restricted Administrative Units for Conditional Access policies it’s smart to use a naming convention that makes sense.
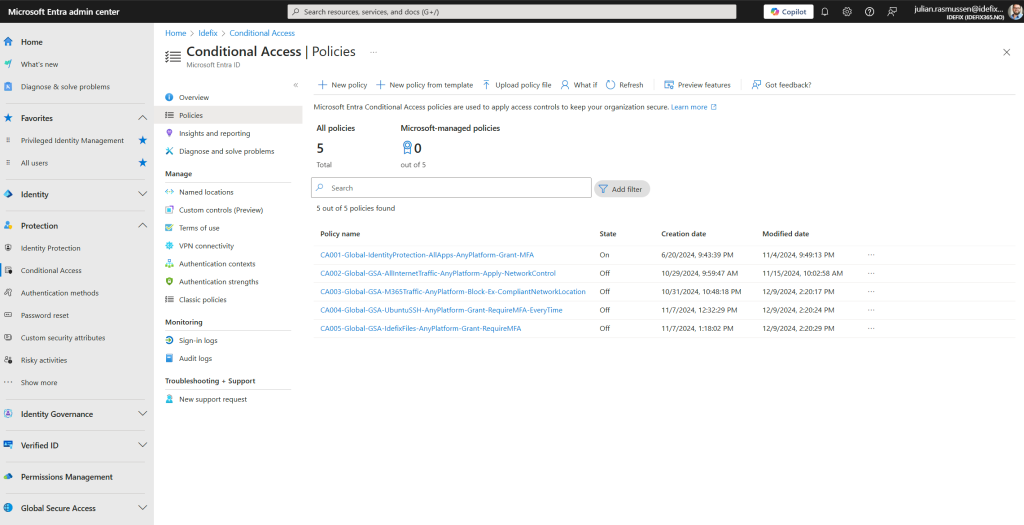
In my demo environment I have these Conditional Access policies, So if I want to create a Restricted Administrative Unite for my CA001 rule, then I would add a naming like this.
CA001-Restricted-Admin-Unit-Excluded-Groups and by doing it this way we can connect the dot’s so that we know that this Admin Unit is for this explicit Conditional Access rule.
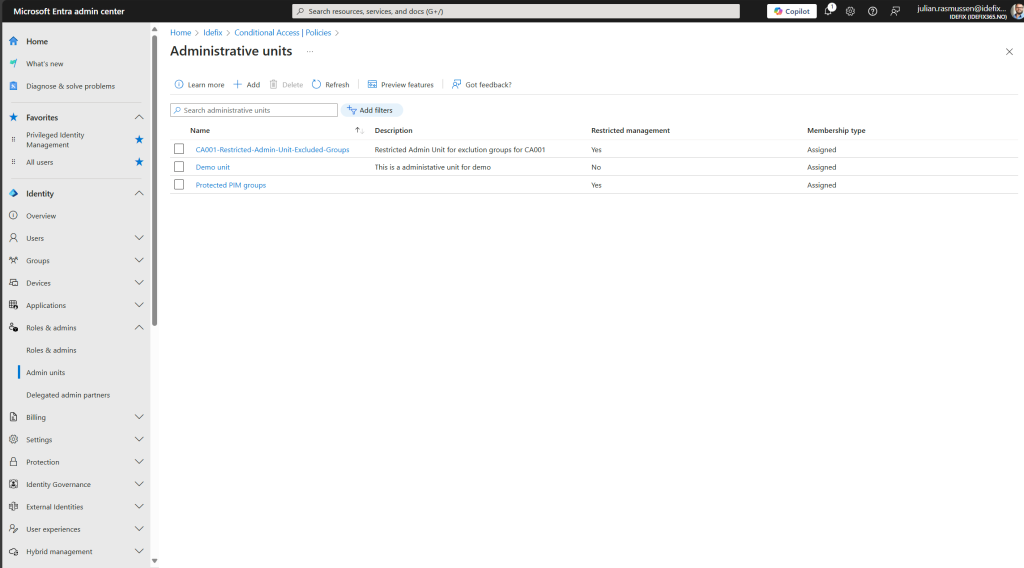
As we see on this last picture here I have created a Restricted Administrative unit in Entra ID. And that is so super easy!
Navigate to entra.microsoft.com and head over to “Identity –> .. Show more –> Roles & admins –> Admin units”
From here we hitt the “+ Add” button and that get’s us into the tutorial for creating a Admin unit.
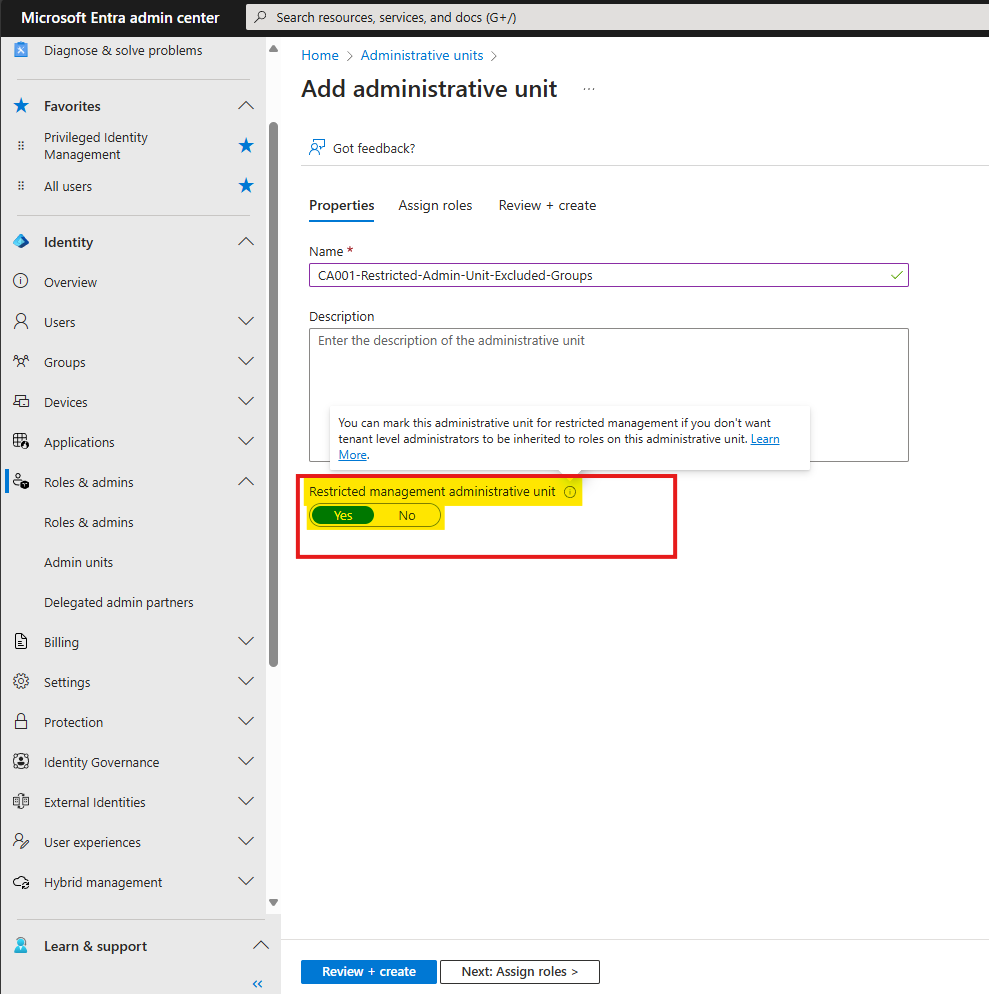
Here we just give it a name following our naming convention, and in this case “CA001-Restricted-Admin-Unit-Excluded-Groups”
And the most important thing is that we need to use the new setting “Restricted management administrative unit”
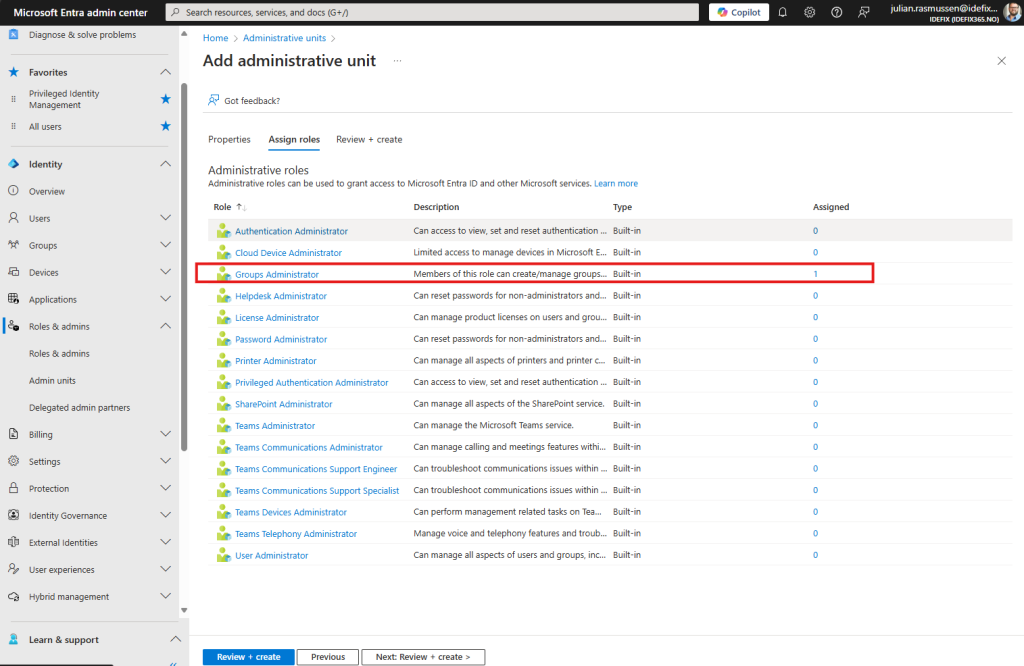
as we move to the next part witch is “Assign roles” we here need to add who are going to be able to manage objects we add to this Admin unit.
(And since we have a restricted admin unit, other admins and global admins are not able to do any changes on the objects that we add into this AU)
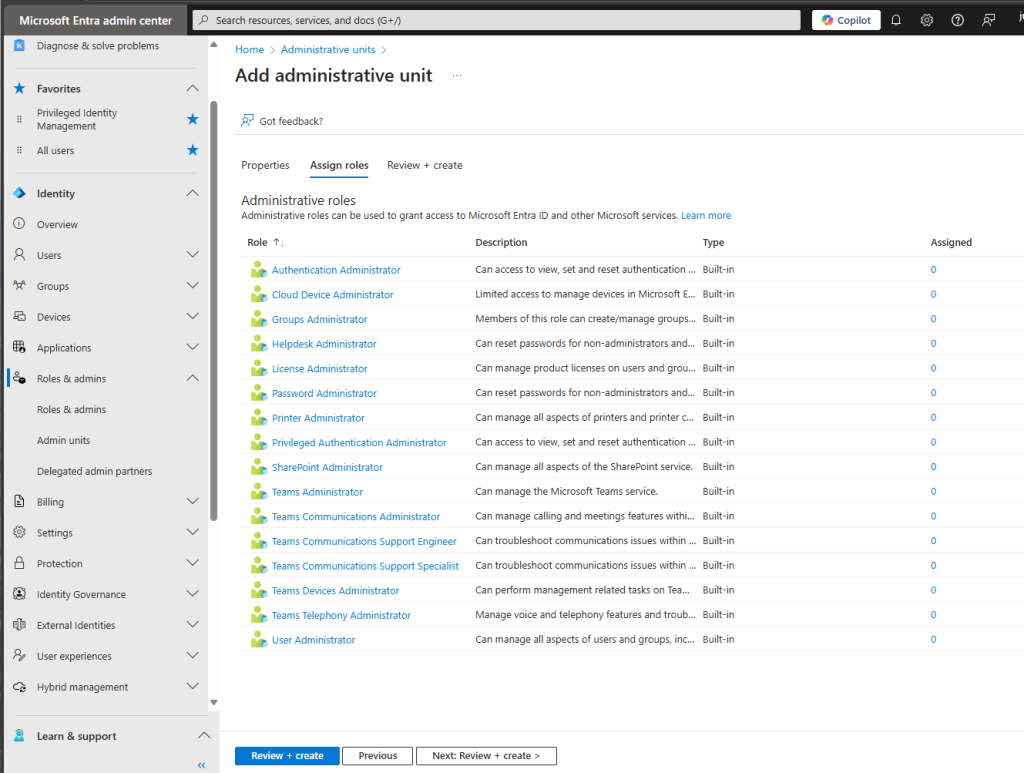
I will add a “Group Administrator” in my case “Dachshund Dash”.
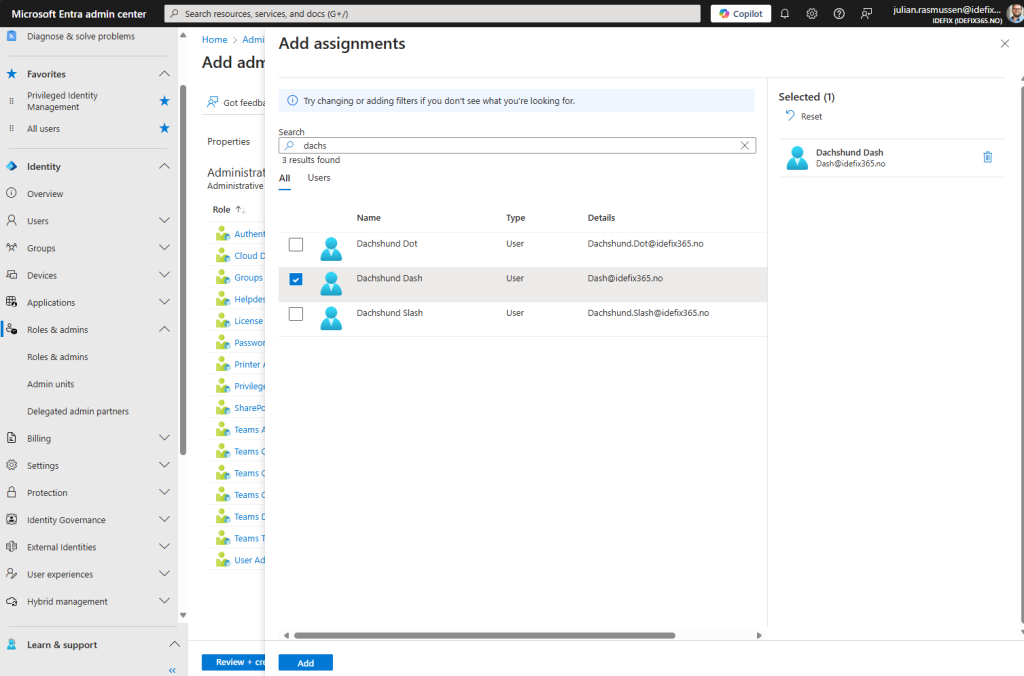
We then go to “Review + create” and take a check over the settings so that we are sure we have it correct (not mutch to do as it’s only name, description and assignments to do here :))
So at this point we have a Conditional Access policy and a Restrictive Admin unit that has Dachshund Dash assigned as Group Administrator for all groups added to the AU.
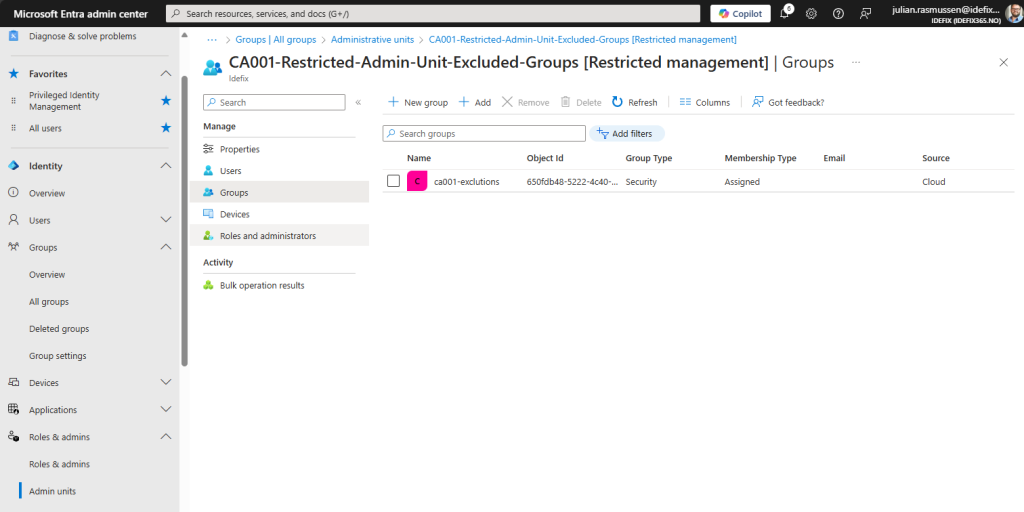
If we navigate into the newly created Administrative Unit and head over to “Groups” we can then add our exclution group witch in my demo environment is called “ca001-exclutions” as you see I keep the CA rule name in all connected parts so that we know all the moving parts and it’s easy to see that they are connected.
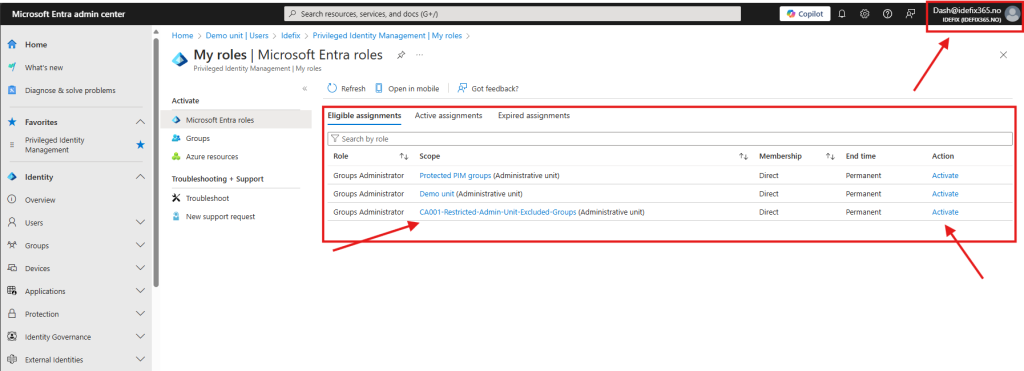
If we then login with Dachshund Dash to Entra Admin center we can see that he has new eligable roles that can be enabled. In this case several Administrative units, but not a global “Group administrator” role for the entire tenant.
Summary
What we have accomplished here now is that we have locked down who can do changes on groups that gives excludes into our Conditional Access rules.
This is a critical factor if you have a lot of administartors in your environement, and you want to close down a loophole where users can exclude them self from critical policies like enforced MFA, contry blocks and so on. By levaraging Restricted Management we can really have full control over who can do what on what Entra objects. And remember, Administrative Units with Restricted Management can protect more that only groups as we also have support for Users and Devices as well as groups.
If you want to learn more about this feature, have a look at Microsoft Learn – https://learn.microsoft.com/en-us/entra/identity/role-based-access-control/admin-units-restricted-management?WT.mc_id=SEC-MVP-5005095




