So now a days many have enabled MFA for their accounts. And that’s great!
It show`s that what we have been working on the last years is working. According to Microsoft, MFA can prevent 99,9% of attacks to your accounts. But there is a attack vector that not many think of.
Do you have full control over the process of onboarding new users?
We often se that users are created and activated several days before the user is actually starting to work. That means that in most of the onboardings the user account is not protected to MFA until the user is sign in in and enters the security information needed for activating MFA on the account.
What we see now is that hackers are executing brute force attacks on username and password of accounts that had never logged on into Azure AD.
So to protect us from this we need to establish a Conditional Access policy preventing users from the ability for enrolling to MFA except from when they are seated at the company (Location whitelist).
Steps for protecting your users
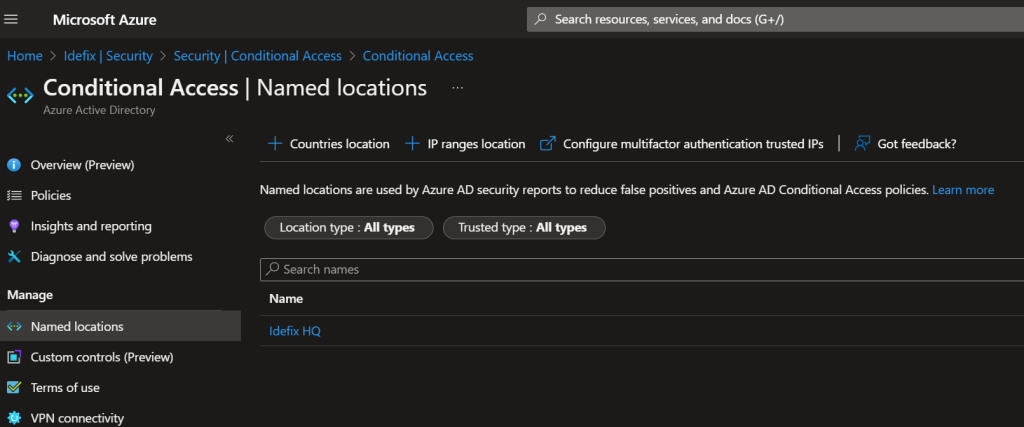
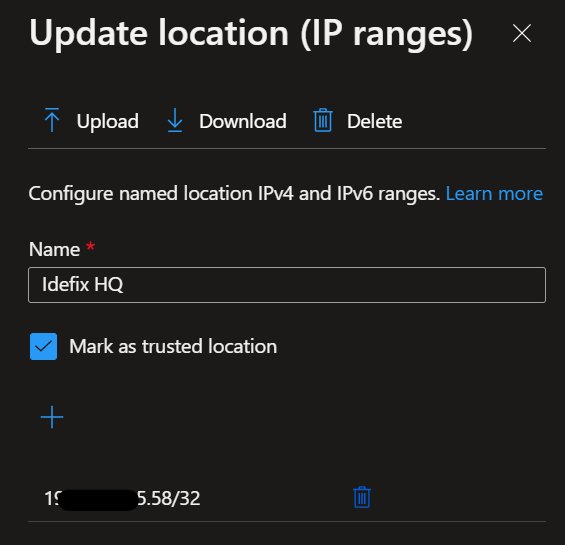
- Login to portal.azure.com and navigate “Azure AD” then head into “Security” -> “Conditional Access” -> “Named Locations” and create a new “IP ranges location”
- Navigate “Policies” and hit “New policy” – then fill in a name for example; “require trusted location for MFA registration”.
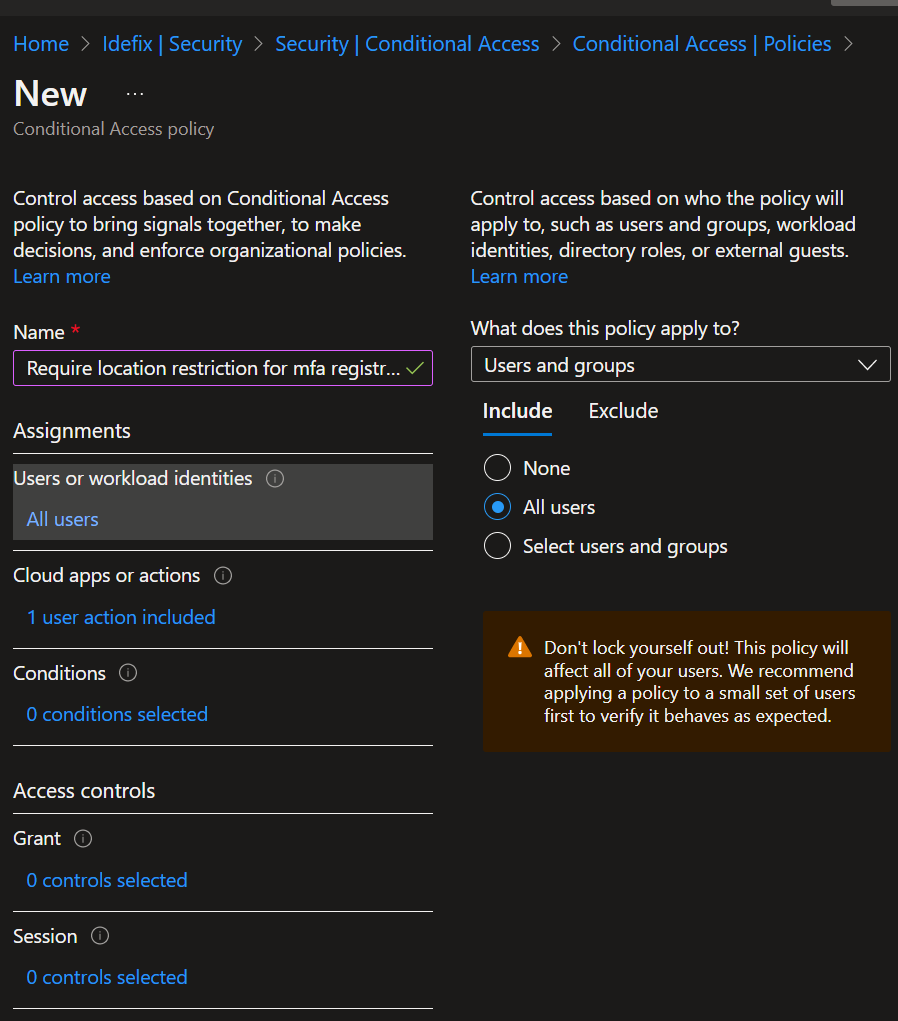
- Select “All users” in the “Users or workload identities”
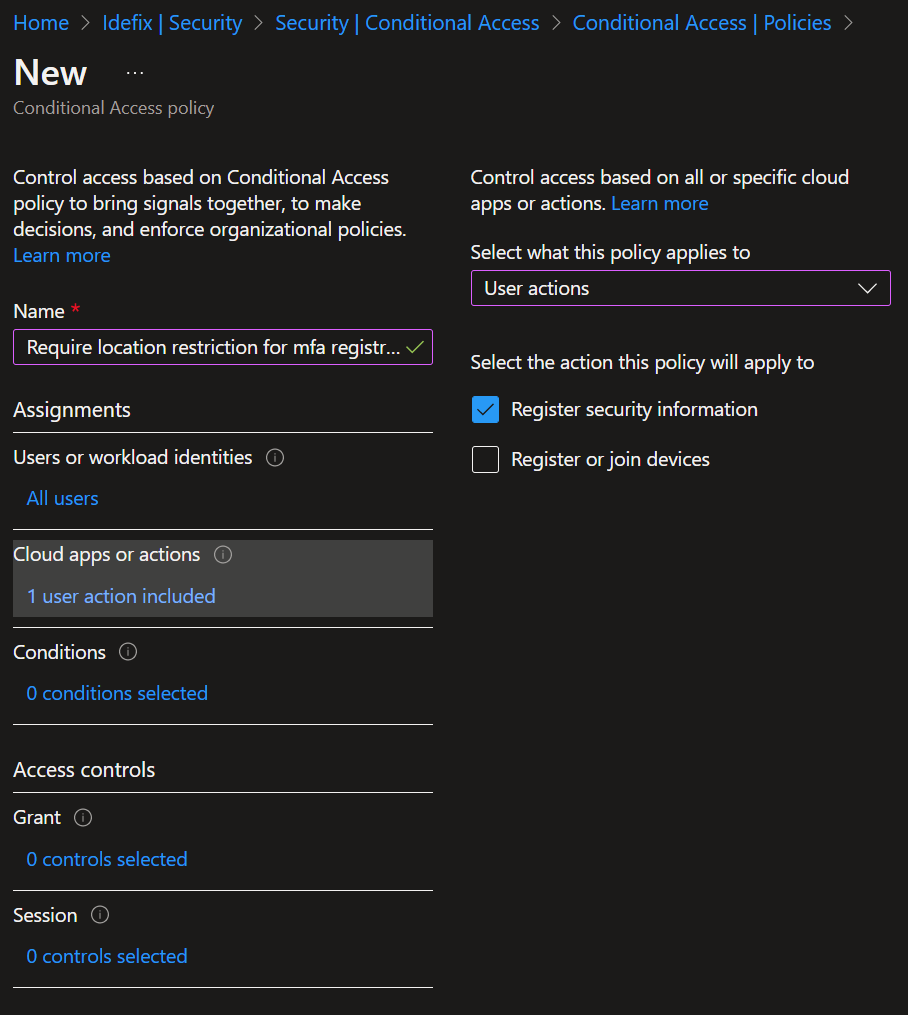
- Select “User actions” in the “Cloud apps or actions” section and checkmark the “Register security information”
- Select “Locations” under “Conditions” and set “Configure” to yes and hit the “Exclude” section and there add your Named Location.
- Go to “Grant” and select “Block Access”
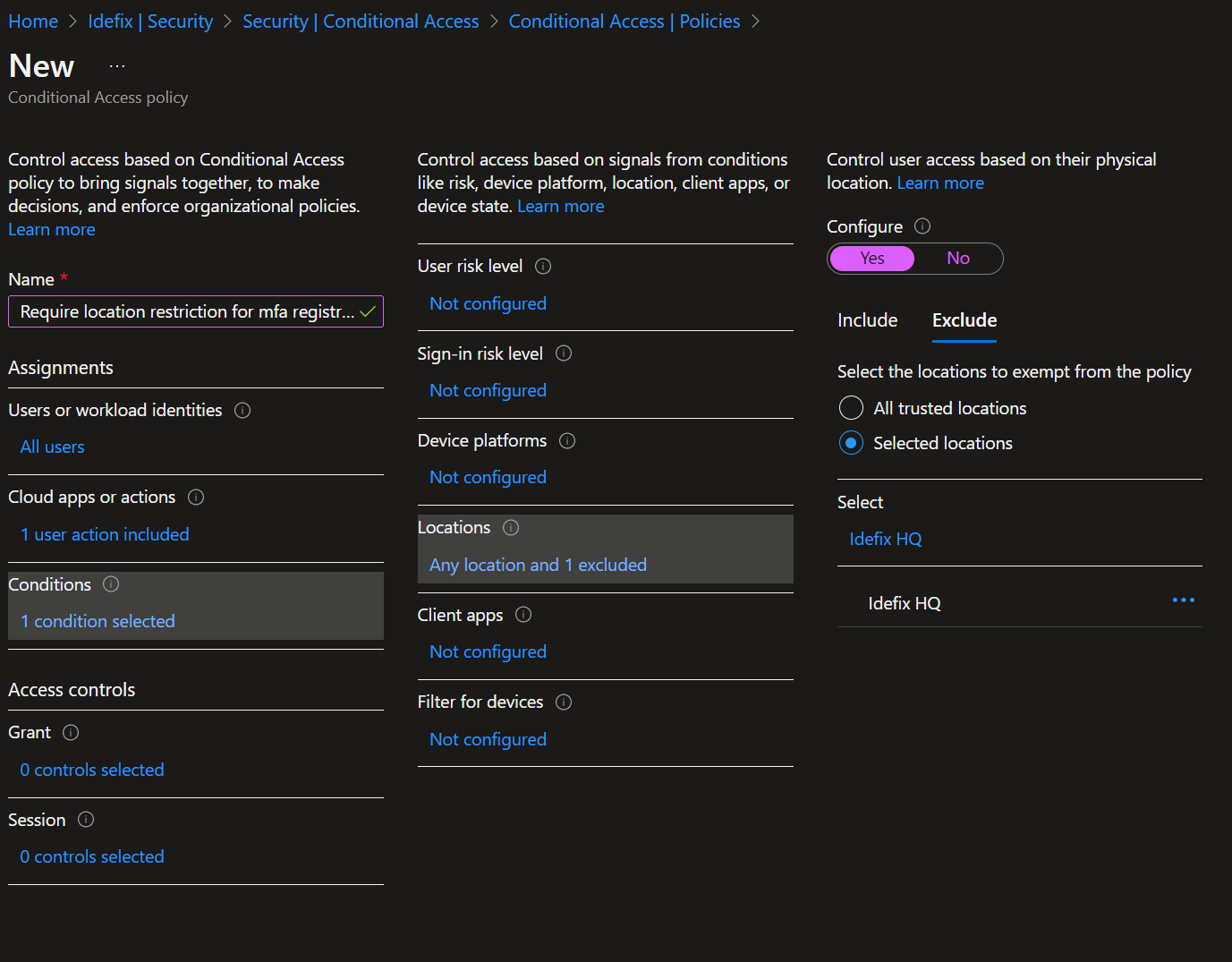
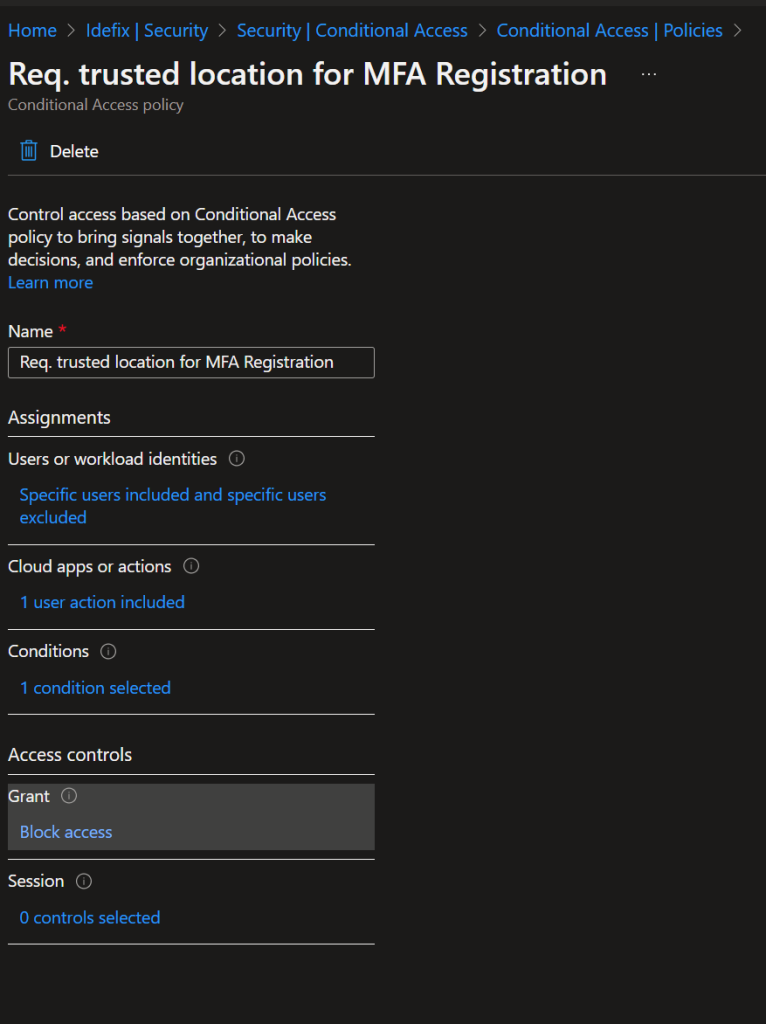
- Now your accounts need to be located at your named location to be able to do a registration of security information.