Main goal
Main goal for this blogpost is to gain more knowledge on how to collect logs from Azure AD. By default you`ll get 30 days audit and sign-in logs stored within Azure AD. To be able to interact / automate on the logs we need to move the logs to a Log Analytics Workspace. So by doing so we gain these and much more features on our log data:
- Ability to automate actions based on logs
- Increase retention time on logs
- Connect Microsoft Sentinel
Speaking of retention time you can choose from 30, 31, 60, 90, 120, 180, 270, 365, 550, and 730 days within the Azure Portal on the Log Analytics Workspace.
Log Analytics
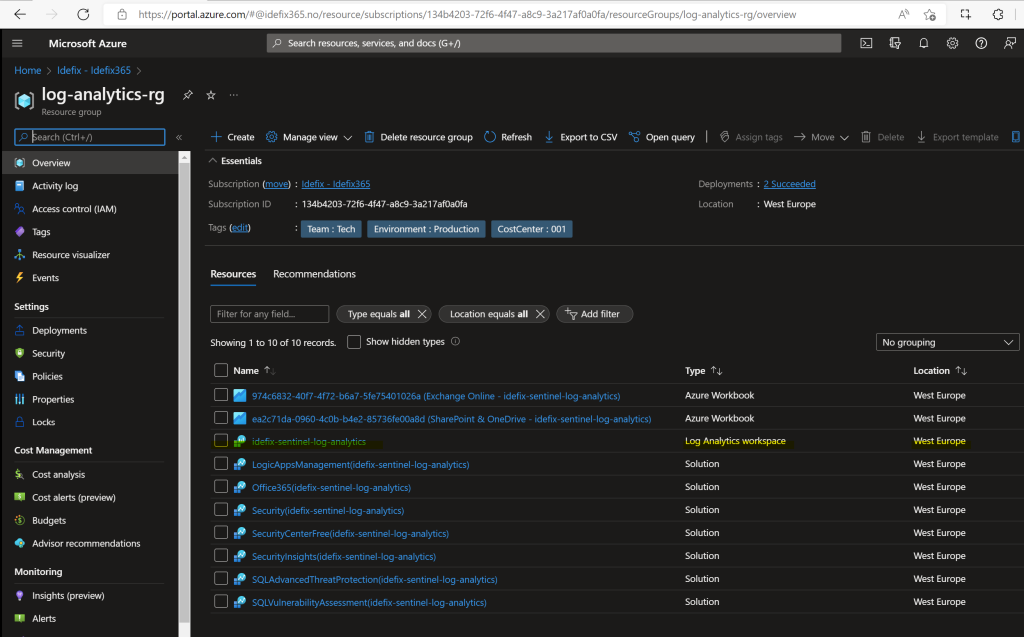
First of all you need to create a Log Analytics Workspace and to do that you need to have a Azure Subscription in place (and you need Contributor access to it).
– Create a “Resource Group”
– Create a “Log Analytics Workspace
Azure AD configuration
When the LAW (Log Analytics Workspace) is ready then you can configure Azure AD to send log`s directly to it.
Head into Azure AD and navigate to “Audit Logs” or “Sign-in logs” and from there click the “Export Data Settings”
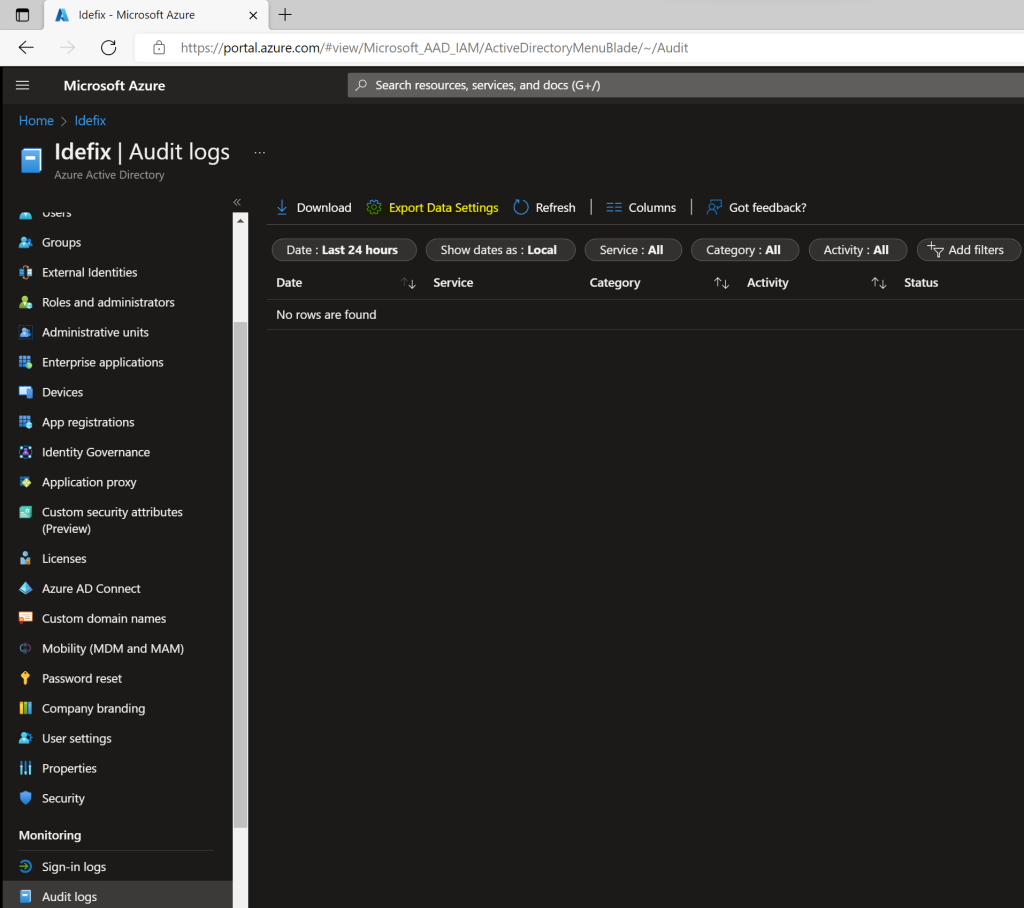
Here you click on “Add Diagnostics Settings” and give it a name, point it to the log analytics you created and choose what to store into that LAW.
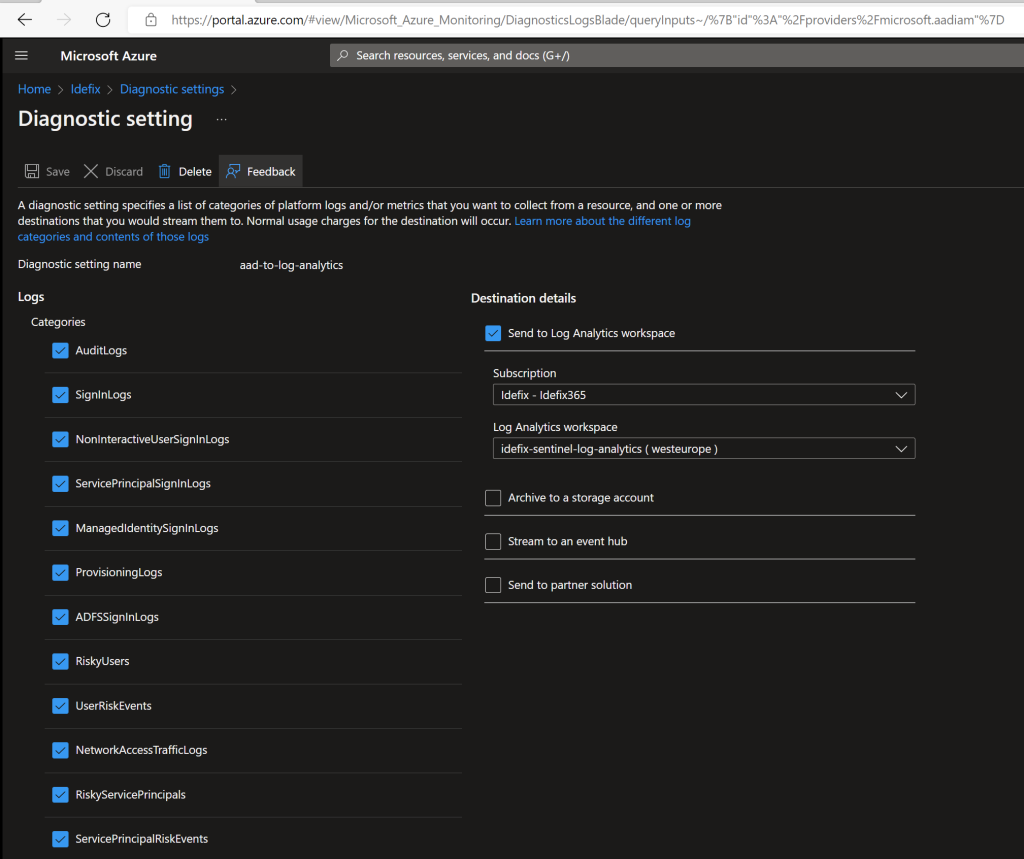
After you save it you should wait about 15-20 minutes before trying to query the logs, just to be sure that new log`s have been streaming into LAW.
Test query in Log Analytics
To query your data you need to navigate to your Log Analytics Workspace and head into the “Logs” pane and from there you can add a Query to search the log`s with.
This query gets all login entries for users whose name contains Julian
SigninLogs
| where Identity contains "Julian"To be more specific, use UserPrincipalName:
SigninLogs
| where UserPrincipalName == "julian.rasmussen@idefix365.no"All sign-ins for Julian in the last 30 days
SigninLogs
| where UserPrincipalName == "julian.rasmussen@idefix365.no"
| where TimeGenerated > ago(30d)