Description
So we now have a new feature that`s awesome!
Have a look at Authentication Context within Azure AD Conditional Access.
What we can do with this is to force difference authentication methods for certain applications based on Conditional Access or we can use this to be able to force for example a FIDO2 authentication when using Privileged Authentication Management for elevating ourself for a role. That role can be within Azure AD or Azure RBAC for that matter.
Setup of Authentication Context + Conditional Access + PIM
Pre-req for this to work is that your tenant is already setup and ready for using FIDO2 as a strong authentication method.
Create a new Authentication context
So the first thing we need to do is to create a Authentication Context. We do that by heading into Azure AD -> Security -> Conditional Access -> Authentication Context and click on “New authentication context”
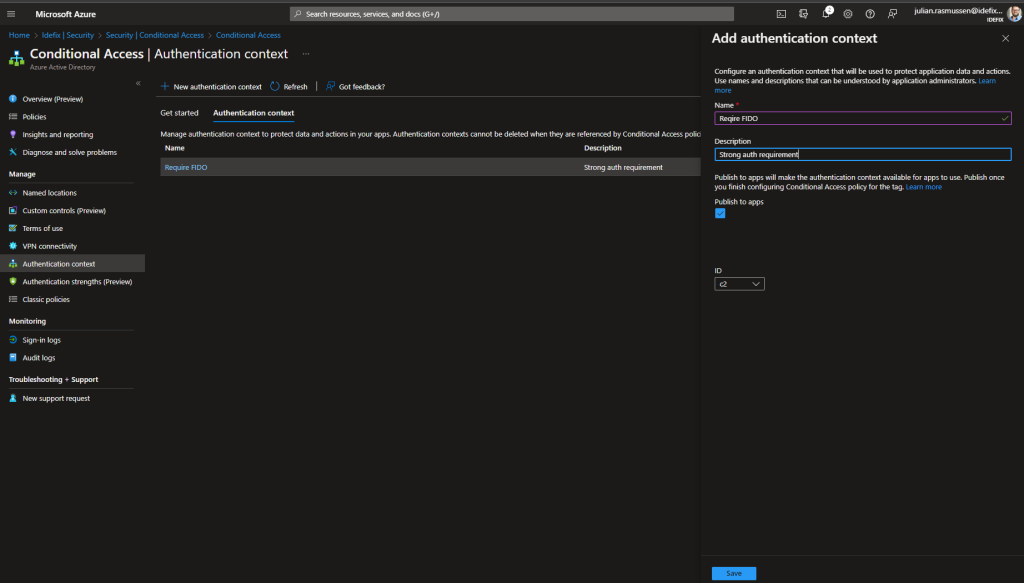
When that`s done – let`s setup the Conditional Access rule that`s going to enforce the FIDO2 for end-users.
Create a new Conditional Access policy
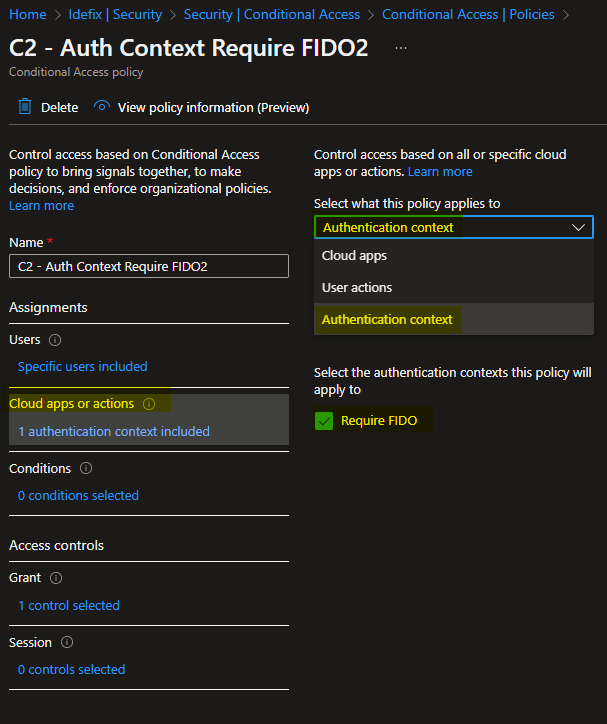
Let`s go to “Policies -> New policy”
- Give it a name for example: “C2 – Auth Context require FIDO2”
- Scope it for “All users”
- Cloud apps or actions -> Set this to “Authentication context” and then choose the context that you created (in my case: Require FIDO).
- Grant -> here we setup the usage of “Require authentication strengt” and choose “Phising-resistant MFA”
- Save it!
Setup a PIM role to use Authentication Context
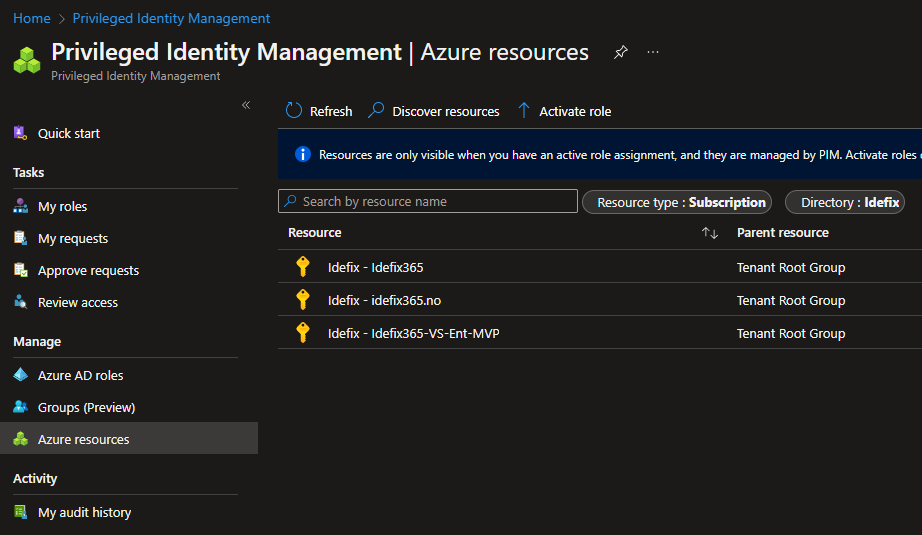
Head into PIM and navigate to “Azure Resources” and go into one of your subscriptions.
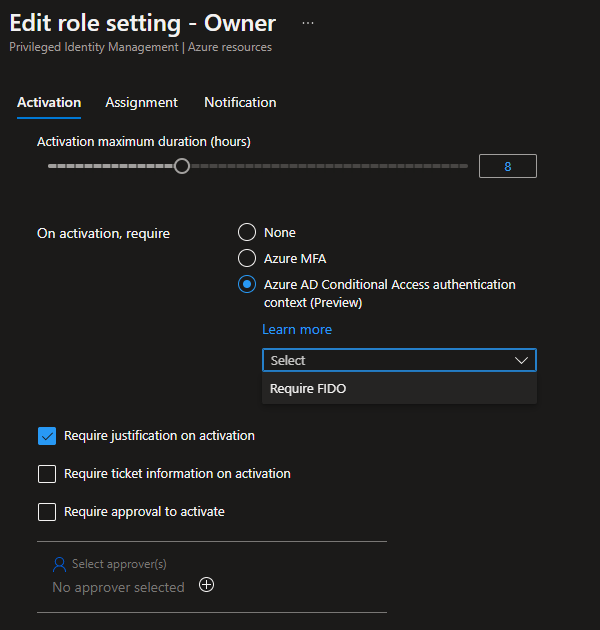
Next click on “Manage -> Settings” then find a RBAC role you want to make more secure. In my case i use thos for the Owner or User Access Administrator roles. When heading into the selected role click on “Edit” and change the “On activation, require” setting to match your Authentication Context that we created earlier and click update.
End user feeling
So when a end-user want`s to elevate to Owner for a subscription that is protected by a Authentication strength this is how it looks in Privileged Identity Management
He will be prompted to do an extra verification
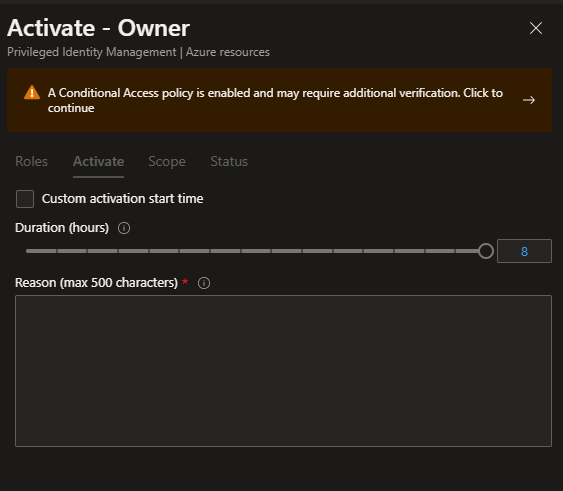
And for me who has FIDO2 enabled and setup on my user it will prompt me to use Windows Hello or Security key to verify my account
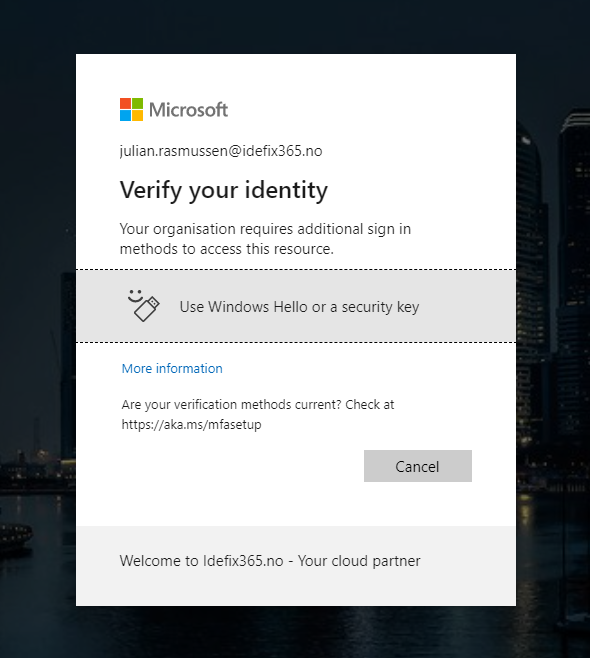
When you have verified your account you can go on and activate the role that you want.
Conclution
When using Authentication Context together with Conditional Access and Phishing resistant MFA it gives admins and owners better segregation and control over privileged roles on their subscription. Here we can use this to require FIDO2 for all roles that can do changes, but maybe just use regular number matching for all other roles like “Reader” or something like that.
PS: Authentication strength is a Preview feature at the moment (08.03.2023) and so is also using Azure AD Conditional Access authentication context (Preview) in Privileged Identity Protection.




