We now have a new capability for choosing different MFA methods for a set of users using Conditional Access policies. And with that we can ensure that our most important users uses the most secure method for authenticating to our services.
Out of the box you can choose from these three MFA methods, but there are options for creating your own method also.
- Multifactor authentication: this is basically the same as the ‘old’ Require multifactor authentication. It will request the user to enter its password and then request the MFA (using the default one the user has configured – MFA request, SMS…). This option does not really strengthen your MFA
- Passwordless authentication: this option requires you have enable the Passwordless authentication method with Microsoft Authenticator https://t.co/89FilYohrQ or FIDO keys https://t.co/6HfQaQrsuR) first. This improves the strength of your MFA authentication
- Phishing-resistant authentication: this option requires you have enable the Passwordless authentication method with FIDO keys https://t.co/6HfQaQrsuR first. This provides the more strength of your MFA authentication
Requirements
To be able to use this feature you need the following
- FIDO 2 activated for atleast your BTG account
https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-authentication-passwordless-security-key - Temporary Access Pass enabled atleast for your BTG account
https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-authentication-temporary-access-pass#enable-the-temporary-access-pass-policy - Global Administrator role in Azure AD
- Your BTG username/password
- A FIDO 2 key
Conditional Access
it`s quite easy to setup the new Conditional Access policy that – go here and do the following – (Azure AD -> Security -> Conditional Access) and create a new policy
https://portal.azure.com/#view/Microsoft_AAD_IAM/ConditionalAccessBlade/~/Policies
Give the new policy a name and set users to your BTG account like this –
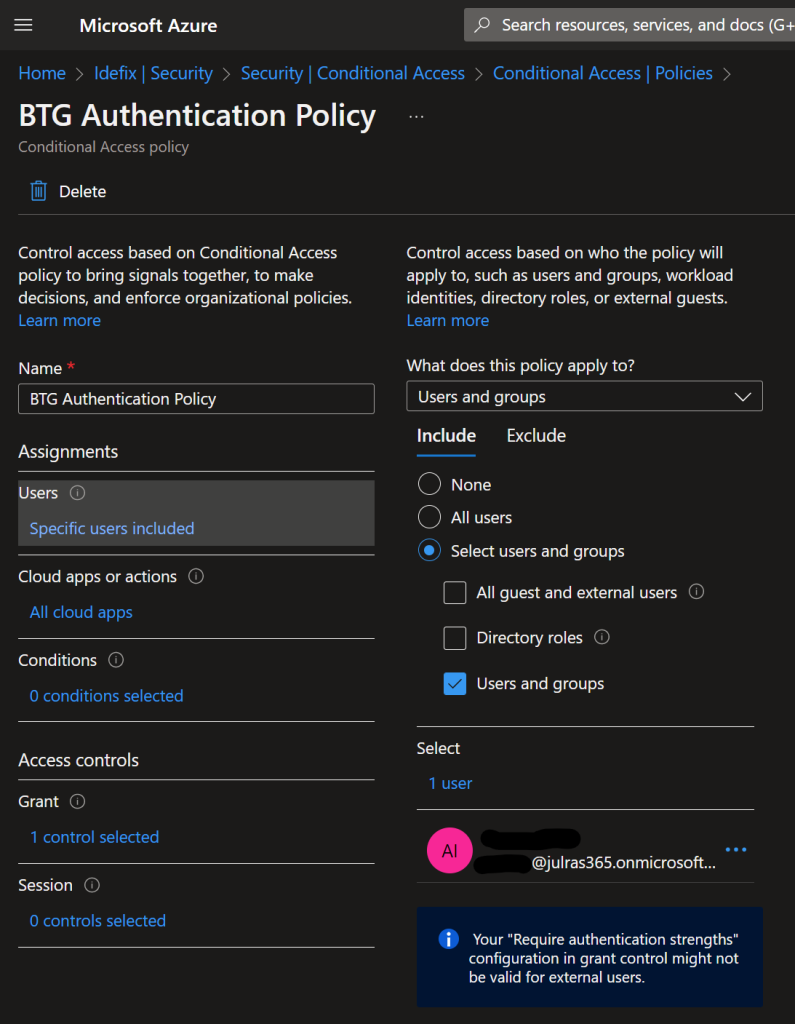
In the “Cloud Apps or actions” section select “All cloud apps” so that we are sure that this account get`s the promt on all applications.
Go to “Grant” and from there you can use the new feature called “Require authentication strenght” set this to “Phising-resistant” and you are good to go!
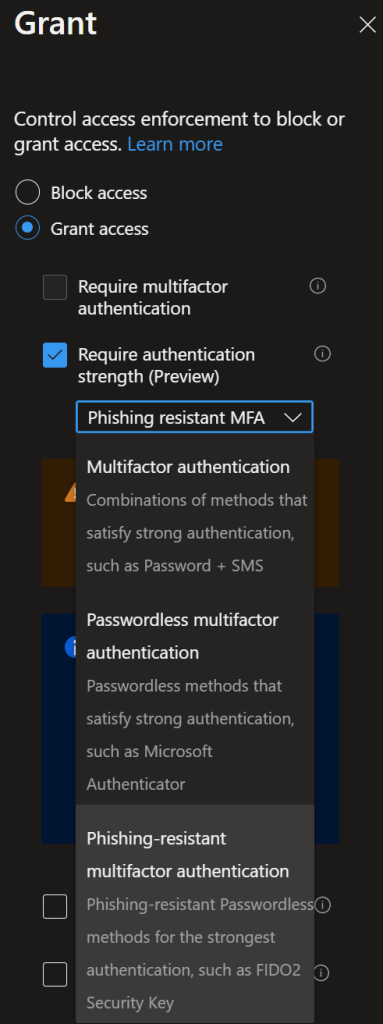
Activate the policy (Enable = On) and hit “Save”
Testing your account
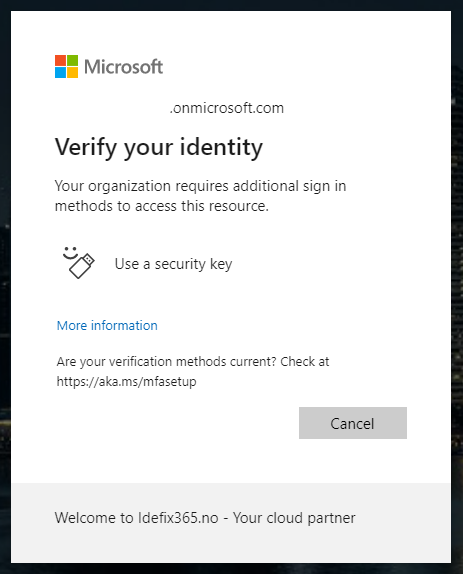
When signing in to your BTG account first time after you enabled the Conditional Access policy that require that your user need`s FIDO2 to be able to sign-in you will be promted by this sign! “Secure your account” – “The organization require that you use one of the following methods to authenticate”
And as we see here – the only option is “FIDO 2 Security key” even tho for the rest of the organization we allow Authenticator App, SMS and Phone calls.
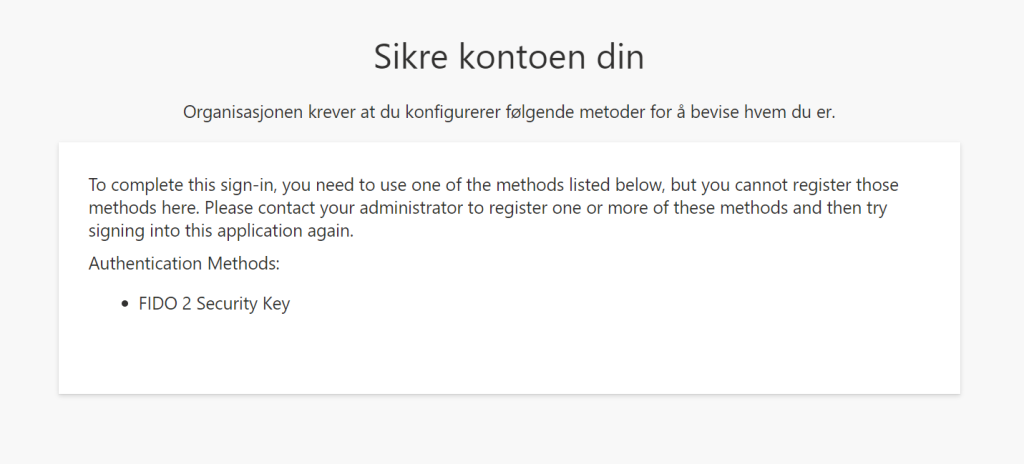
So this message means that we need to use a Temporary Access Pass so that the user can update his MFA method.
Create a TAP for the user on the user object – AzureAD -> Users -> BTG Account -> Authentication methods.
Navigate to https://aka.ms/mysecurityinfo and sign-in with the TAP.
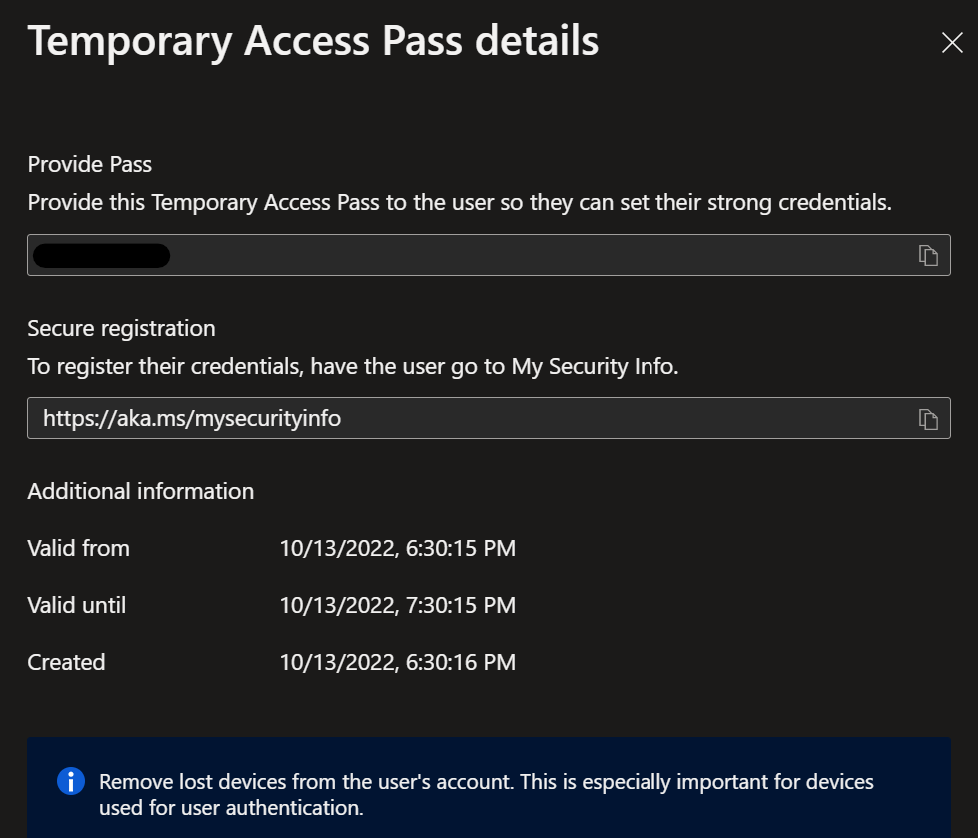
You can then setup your FIDO2 key for your user when you are signing into to https://aka.ms/mysecurityinfo.
Take away`s
Even tho we require FIDO2 key for our user, we still need to authenticate with username and password before we are prompted for the FIDO2 key. This is since Conditional Access policies are only evaluated after primary authentication witch is Username + Password.