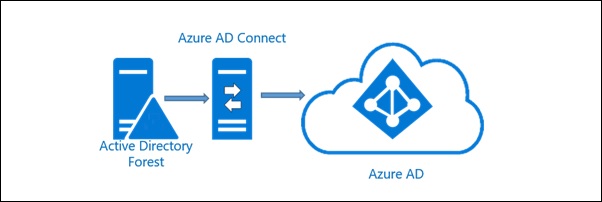
Azure AD Connect sync issues
Now and then we get errors in our Azure AD Connect syncronization, or that said – my customers...
Find unlinked GPOs in your domain
Have you ever wondered if your domain has any GPO without a link and which GPO that would...
Find domain admins with password never expires
Do you know how many domain admins you have in your domain? Do you know which domain admins...
“No logon servers are available” error after installing updates (SBS2008)
Yesterday I was doing maintenance on a Windows Small Business Server 2008, the Windows Update patches installed successfully...
Check for Active Directory replication failures
A quick and easy way to check your Active Directory for any replication errors using Powershell. Get-ADReplicationPartnerMetadata -Scope...
AD: Windows Time configuration
Domain controllers It is ONLY the domain controller holding the PDC role that should use external NTP. All...
Find disabled users with their group membership and remove them from their groups
To quickly see the disabled users and their group membership in your Active Directory you can use this...
Transfer or seize FSMO roles with powershell
To transfer all FSMO roles from one DC to another you can use the following line in powershell: ...
DFS Replication error on Domain Controllers
If you have DFS replication errors on one or more domain controllers, first find out witch domain controller...
