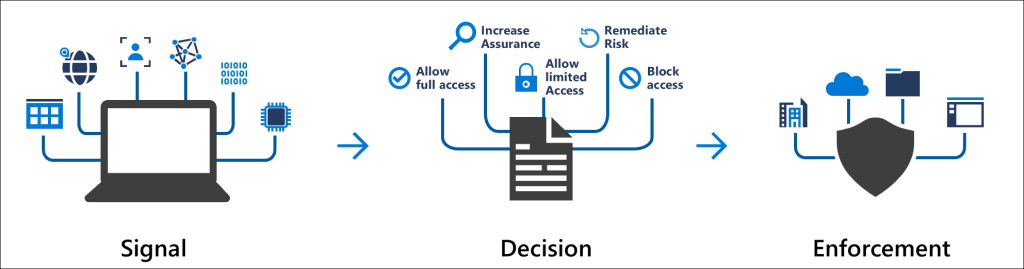
Security Defaults – a lifesaver for some and a little pain for others
So lets talk about “Security Defaults” a bit, this new feature in AzureAD who replaces “Baseline policies: ”...

AIP is deprecated, move to Unified labels now!
At 06.01.2020 Microsoft released the deprication notice for Azure Information Protection client and Label management in the Azure...

How do I know all my users are enabled for and using MFA?
More and more organizations is taking advantage of using MFA for their users and there is no reason...
Automated Investigation & Response
The Automated Investigation & Response feature under Threat management in Security & Compliance admin portal is a pritty...
Get started with MFA – part two
So in the previously post I went through how to activate MFA for Administrator roles i a really...
Get started with MFA – part one
You problably heard about multifactor authentication by now, but have you enabled it in your environment? If not! Please do so at once! I will in this short blogpost give you the direction to get started with MFA in Azure AD. So let`s just jump right into it. First things first – protect your admin accounts! With admin accounts i mean a account who has a additional role assigned other then beeing a regular user and to mitigate these users we will enable a Conditional Access who is requires MFA for all...
