AI can magnify what an organization can do, so making sure that employees, devices, and data stay secure is more important than ever.
Let`s dive into Zero trust a bit. And you may be thinking – What is Zero Trust anyways?
A Zero Trust architecture is a comprehensive security strategy to help you secure your data and prepare your organization for future threats.
Well, let`s zoom into what and how we can protect our self in a Zero trust mindset.
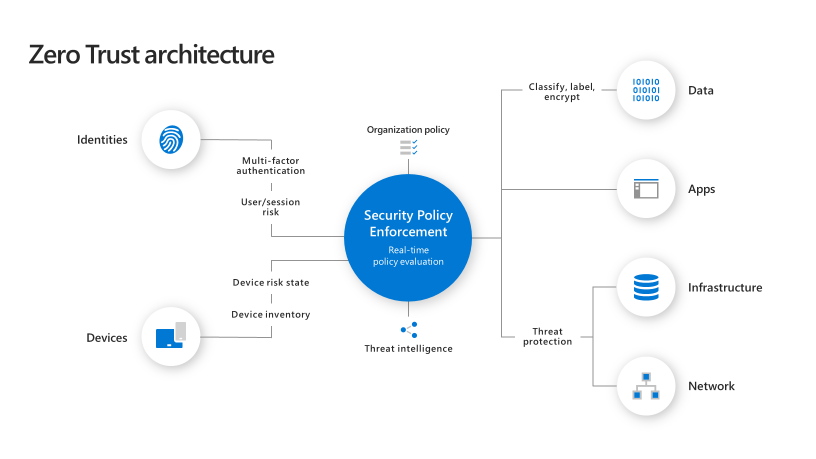
Microsoft`s zero trust approach are resting on three core principles:
- Verify explicitly
- Least privileged access
- Assume breach
These three core principles are key for optaining a good cybersecurity hygiene.
And also you can`t have Zero trust if you don`t have managed endpoints. So make sure you are using the most up-to-date endpoint management will help lay the right foundation for the security in the new era of AI
Endpoint management can help provide data to help customize your AI models, allowing your organization to become more secure and productive faster.
Let´s go into each core pilar.
Verify explicitly
Always make security decisions using all available data points, including identity, location, device health, resource, data classification, and anomalies. But not only for your identity but also by verifying third-party software in your supply chain. So this means that if something can be verified – do the verification so that we have just one more check of who you are and where you are coming from.
Least Privileged access
Limit access with just-in-time and just-enough-access (JIT/JEA) and risk-based adaptive polices and ofcourse this applies for not only filestorage and data, but for the whole infrastructure as well. Here we are aming at both end-users and also administrators or developers. Nobody need`s access to everything at all time – so please restrict access to all data and infrastructure so that access reflects what kind of work you are doing.
Asume breach
Minimize blast radius with micro-segmentation, end-to end encryption, continuous monitoring, and automated threat detection and response. This speaks for it self i guess 🙂
Summary and recommendations
A zero-trust architecture is a critical component to modernizing security posture and ensuring that sensitive data and identies are safe. Even tho it can be complex there are ways to get started and any improvements are better that non improvements. Understand your data landscape and identify sensitive data across your file services (cloud or on-premises) and classify it by sensitivity level.
So please read up on this and start adopting the Zero Trust architecture in your own infrastructure today so that YOUR data is kept safe within YOUR bounderies.
- More than any other single step, enable MFA to reduce account compromise probability by more than 99.9 %.
- Start identifying where and what kind of data your organization is storing.
- Learn more and configure for Zero Trust using Microsofts Zero Trust Deployment Guides





One Comment
Comments are closed.