So these day`s we all uses MFA right? But not all MFA methods are as good as we think.
There have been several cases where “SIM Swapping” or “SIM Hijacking” has been the case and therefor – can we trust using SMS for Multi-Factor Authentication?
In short notes this is how SIM Swapping is done.
- You loose personal information.
- Your information is used to gain trust at the mobile carrier to convice them to switch from current to new SIM card (the new SIM is already in the hands of the bad guy)
- With controll of mobile number the bad guy log`s onto your services with one-time password or completing MFA challenge.
- Your account is compromised
With that said, you should disable SMS as an authentication method.
See my other blog post on how that`s done!
Since you now uses Microsoft Authenticator as your primary MFA factor you get a push notification with “Allow” or “Block” access whenever the authentication is done.
At this point the bad guy start using a method called “MFA Fatigue attacks” and blasts lot`s of authentications against you, and somethimes a user clicks on “Allow” and thinks; “It`s most likely my phone or tablet or something…”.
But with the new capabilities from Microsoft within using Azure MFA you can now add “Number matching” and “additional context” to the signin (both features are in preview at the momemt (04.05.2022).
OK – so here`s how it looks!
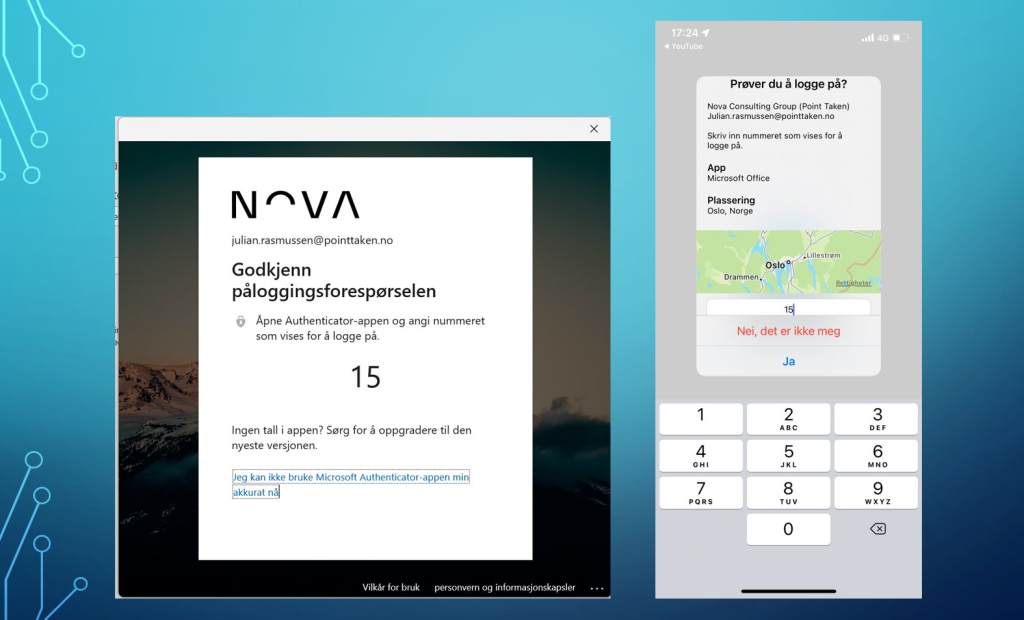
So you see that when ever the authentication is done a number is shown and it needs to be matched on your Microsoft Authenticatior application. In addition we also see a map and location of where the authentication is getting from!
Here`s how you can configure it!
- Head over to portal.azure.com
- Navigate to Azure AD -> Security -> Authentication methods and click on “Microsoft Authenticator”
- Hit “Add users and Groups” and add a group or user to test with and click “Select”
- Then open the settings of the group and “Require number matching” and “Show additional context in notifications”
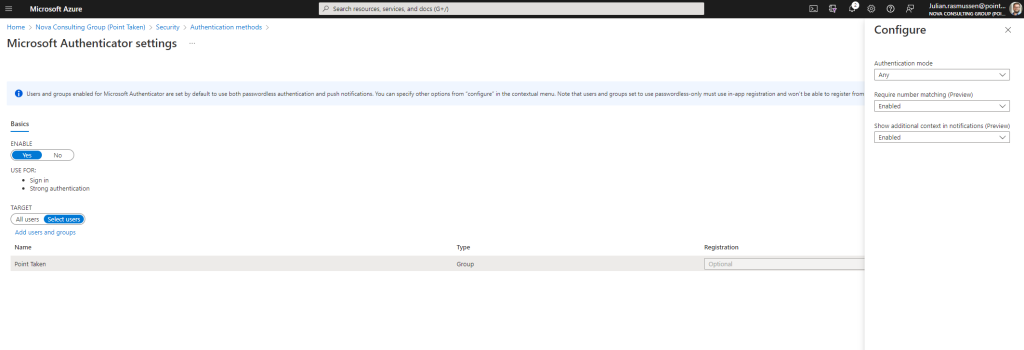
There you have it!
Next time you authenticate with a user that`s configured to this setting you will get a number matching 🙂




